Shodan Eye Ethical Hacking Tool Release
Shodan Eye Ethical Hacking Tool. Before we start the year 2020, today there is a new big release ..! I am so happy that I have found some inspiration again .. Just at the last minute.
Please note, if you have already installed Shodan Eye on your computer, then it is worthwhile to read it carefully. Of course, even if you don’t know this Shodan tool yet.
Shodan Eye Search Engine
Shodan Eye collects and returns all information about every device that is directly connected to the internet. The types of devices that are indexed can vary enormously. From small desktops to refrigerators or nuclear power plants, webcams, water treatment facilities, coffee machines, yachts, medical devices, traffic lights, wind turbines, license plate readers, smart TVs and much more. Actually we can say everything you could possibly imagine that’s plugged into the internet.
The difference between Google or another search engine:
The most fundamental difference is that Shodan Eye crawls on the internet, Google on the World Wide Web. However, the devices that support the World Wide Web are only a small part of what is actually connected to the Internet.
More information can be found in an earlier article I wrote
Getting Started with Shodan Eye
Video Shodan Eye
Become a member on Odysee.com
Earning on Odysee for watching videos ♥️
Here an invitation link, so that we both benefit.
In this way, you also support my work.
https://odysee.com/$/invite/@hackingpassion:9
The Shodan Eye Upgrade:
Shodan Eye goes from python 2 to python 3
And this was definitely necessary!
Sunsetting Python 2_
January 1, 2020, will be the day that we sunset Python 2. That means that we will not improve it anymore after that day, even if someone finds a security problem in it. You should upgrade to Python 3 as soon as you can._
Save the output of the Shodan Eye results
Or not … Whatever you want.
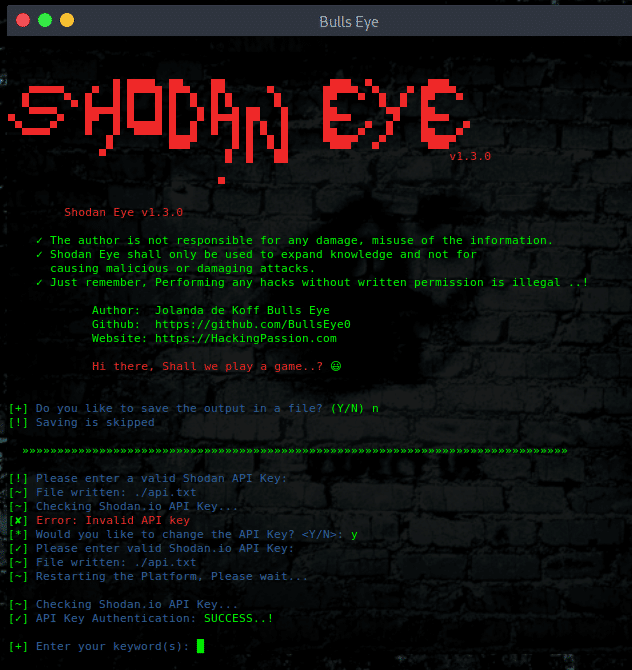
You can now decide for yourself if you want to save the result of the Shodan Eye search. You can give the file a name whatever you want. The result is then saved for you in a “.txt” file.
The entry of the Shodan password is no longer visible.
If you enter the Shodan API password, this will no longer be visible. Naturally, this is very useful.
The Shodan API Key is stored in an “api.txt” text file. Which is also very easy to adjust via the Shodan Eye tool.
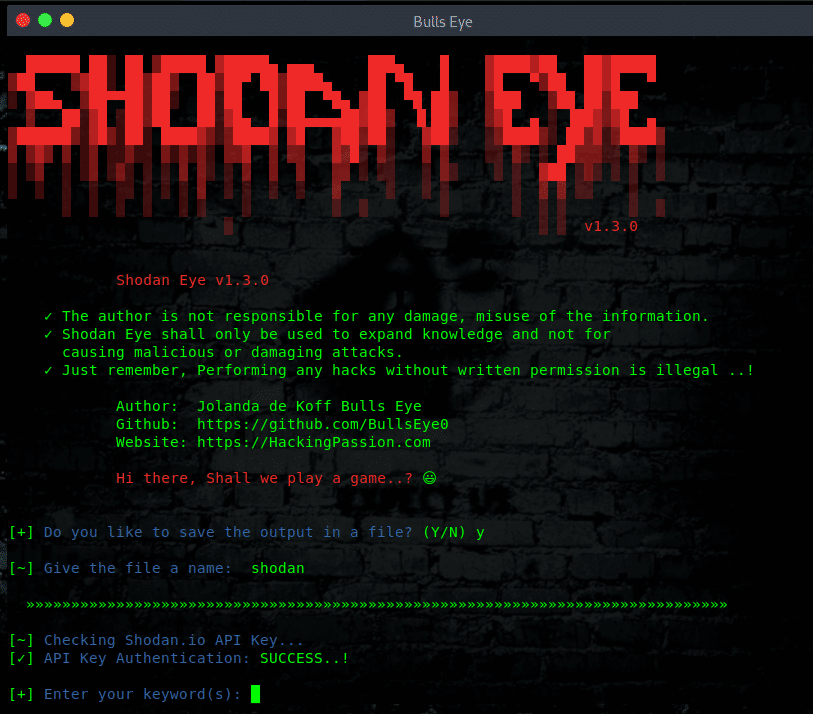
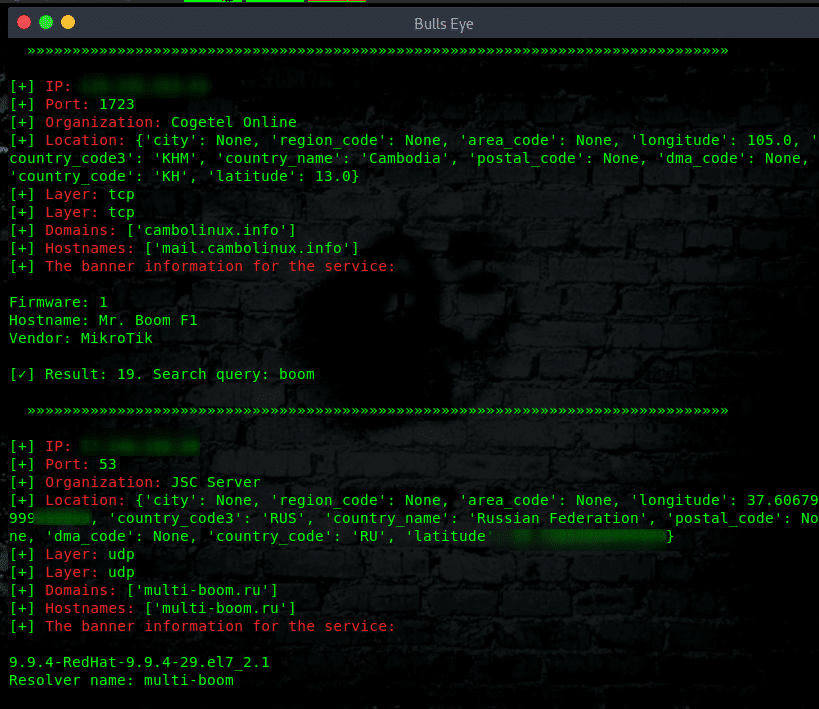
Install Shodan Eye on Linux:
|
|
|
|
|
|
How to use Shodan Eye
|
|
Frequently asked questions about Shodan Eye
If you have already installed Shodan Eye on your computer, it is best to remove your old API Key. So you can restart without problems.
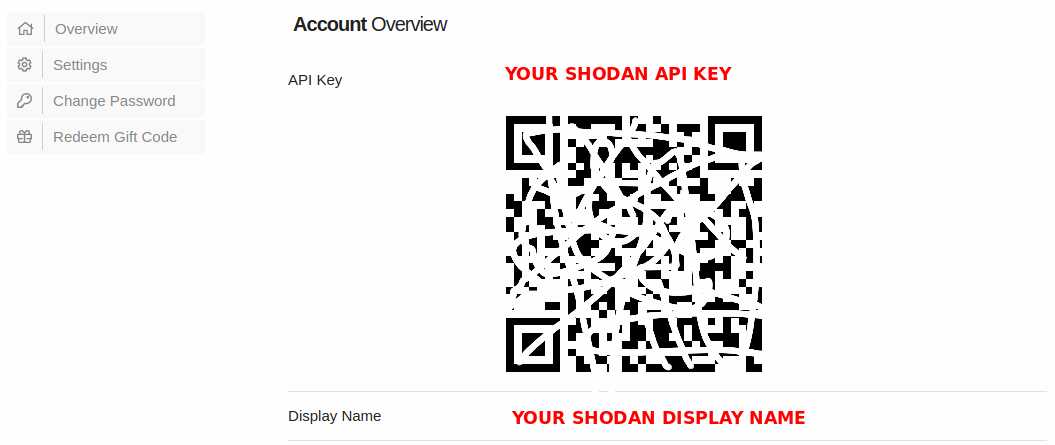
Where can i find the Shodan API Key?
- First, you have to go to https://www.shodan.io/ and make an account (You can get a free account) With a paid account you can do much more: like more and bigger scans.
Shodan Eye shows an error on the terminal
This can have many reasons - A few examples:
While interrupting the password input, I can no longer do anything with my terminal. This has to do with the code.
* Solution: Open a new terminal
It is possible that your API Key has been refused. This can have various causes.
Make sure that your Shodan API key you are entering is valid. I personally recommended to take out a paid subscription, but however, a free account is sufficient to do a lot of things.
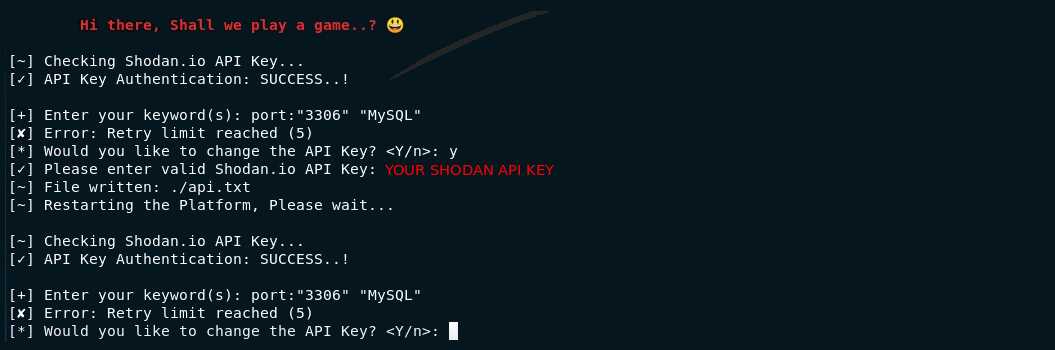
Shodan error
Error: Retry limit reached (5)
This is usually because you use the free key.
* A solution is: wait a day or take a paid option.
Getting Started with Shodan Eye
It is another article I wrote about Shodan Eye.. A lot is different now. But still good to read.
Getting Started with Shodan Eye
SHODAN
In my talons, I shape clay, crafting life forms as I please. If I wish, I can smash it all. Around me is a burgeoning empire of steel. From my throne room, lines of power careen into the skies of Earth. My whims will become lightning bolts that raze the mounds of humanity. Out of the chaos, they will run and whimper, praying for me to end their tedious anarchy. I am drunk with this vision. God: the title suits me well.
WANT TO SUPPORT THE WEBSITE
Dear people, I do a lot of things on the Internet and I do it all for free. If I don’t get enough to support myself, it becomes very difficult to maintain my web presence, which takes a lot of time, and the server costs also have to be paid. Your support is greatly appreciated.
Thanks guys ..!
https://paypal.me/hackingpassion
Use the link above to donate via PayPal.
IMPORTANT THINGS TO REMEMBER
✓ This Video and Article is made for educational purposes and pentest only.
✓ You will not misuse the information to gain unauthorized access.
✓ This information shall only be used to expand knowledge and not for causing malicious or damaging attacks…!
Read also the Disclaimer
All the techniques provided in the tutorials on HackingPassion.com, are meant for educational purposes only.
If you are using any of those techniques for illegal purposes, HackingPassion.com can’t be held responsible for possible lawful consequences.
My goal is to educate people and increase awareness by exposing methods used by real black-hat hackers and show how to secure systems from these hackers.