HackingPassion.com
Hacking is not a hobby but a way of life ♥
BlackArch Linux is an Arch Linux-based penetration testing distribution for penetration testers and security researchers. The repository contains 2521 tools. In this article, I’m going to show you how to install BlackArch. A Step-by-Step walkthrough..!
To be honest, I am completely surprised by what I see now, great progress from BlackArch. How fast it is. Last year was the last time I had BlackArch on a computer. Now tested for a few days, for this article and video.
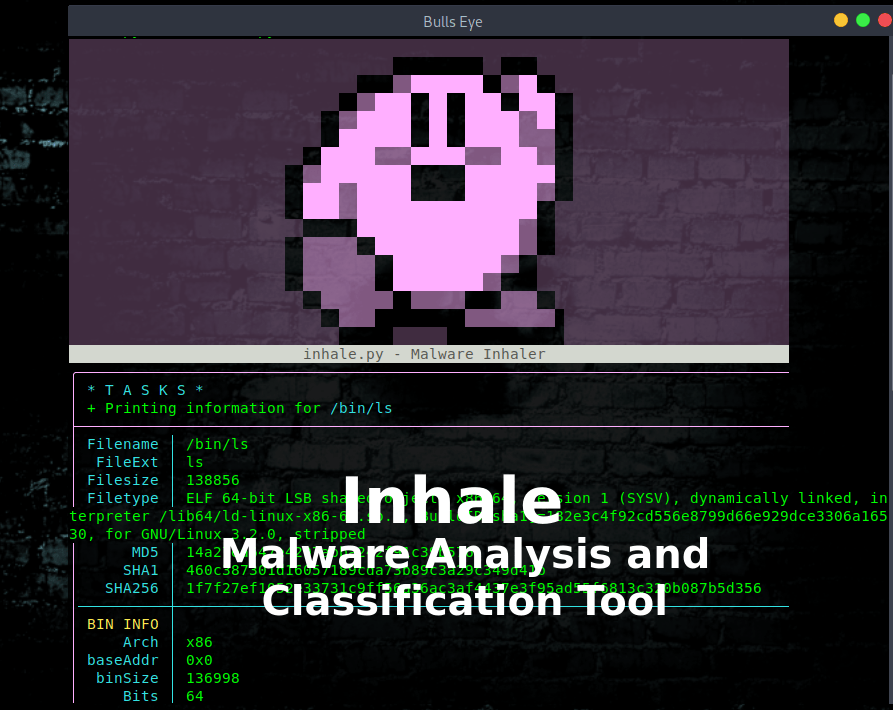
Inhale is a malware analysis and classification tool that is capable of automating and scaling many static analysis operations.
This is the beta release version, for testing purposes, feedback, and community development. Thanks to netspooky The developer of this amazing tool.
Background https://github.com/netspooky/inhale#background
Inhale started as a series of small scripts that I used when collecting and analyzing a large amount of malware from diverse sources. There are plenty of frameworks and tools for doing similar work, but none of them really matched my workflow of quickly finding, classifying, and storing information about a large number of files.
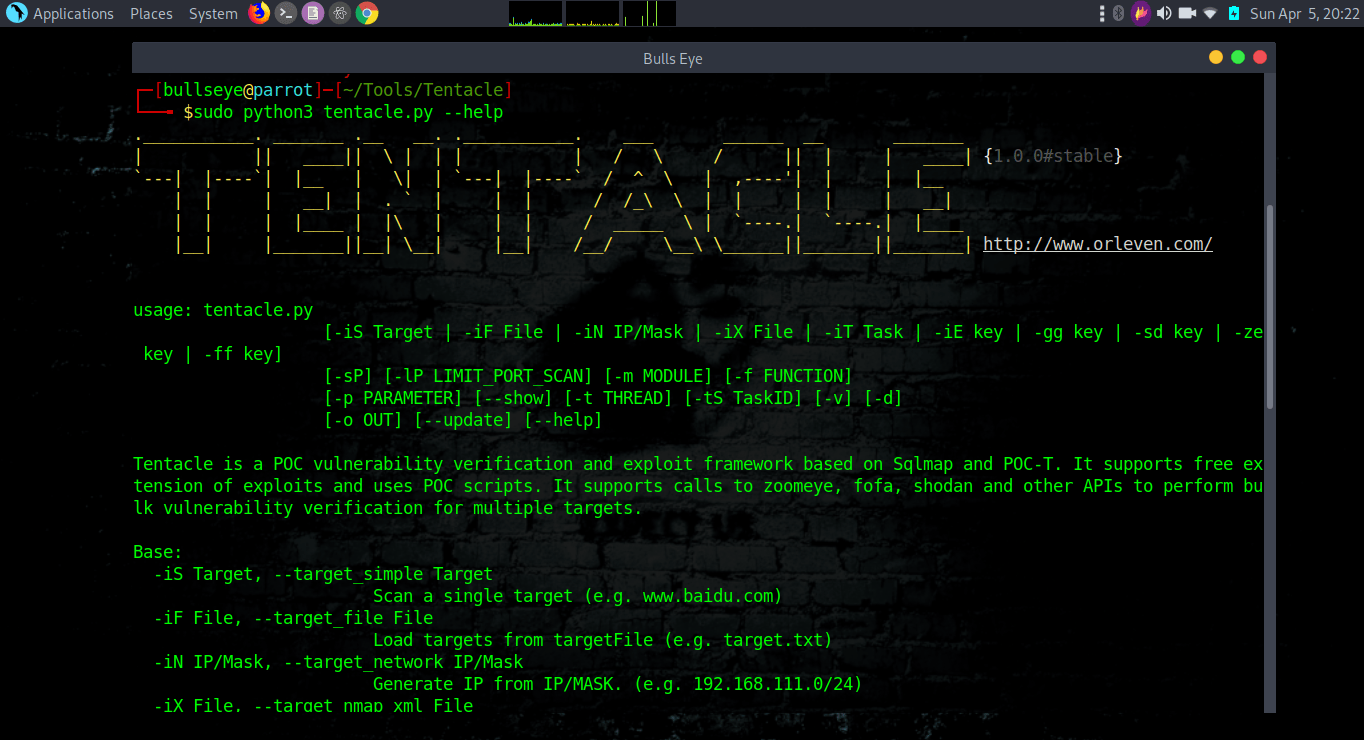
Tentacle is a POC vulnerability verification and exploits framework. It supports a free extension of exploits and uses POC scripts. It supports calls to Zoomeye, Fofa, Shodan, and other APIs to perform bulk vulnerability verification for multiple targets. Tentacle is an open-source vulnerability verification and exploits framework that is coded in Python3. It supports easy addition of exploits and even facilitates bulk vulnerability verification across targets using search engines such as Google, Baidu, Bing and internet-connected search engines such as ZoomEye, FOFA, Shodan, etc.
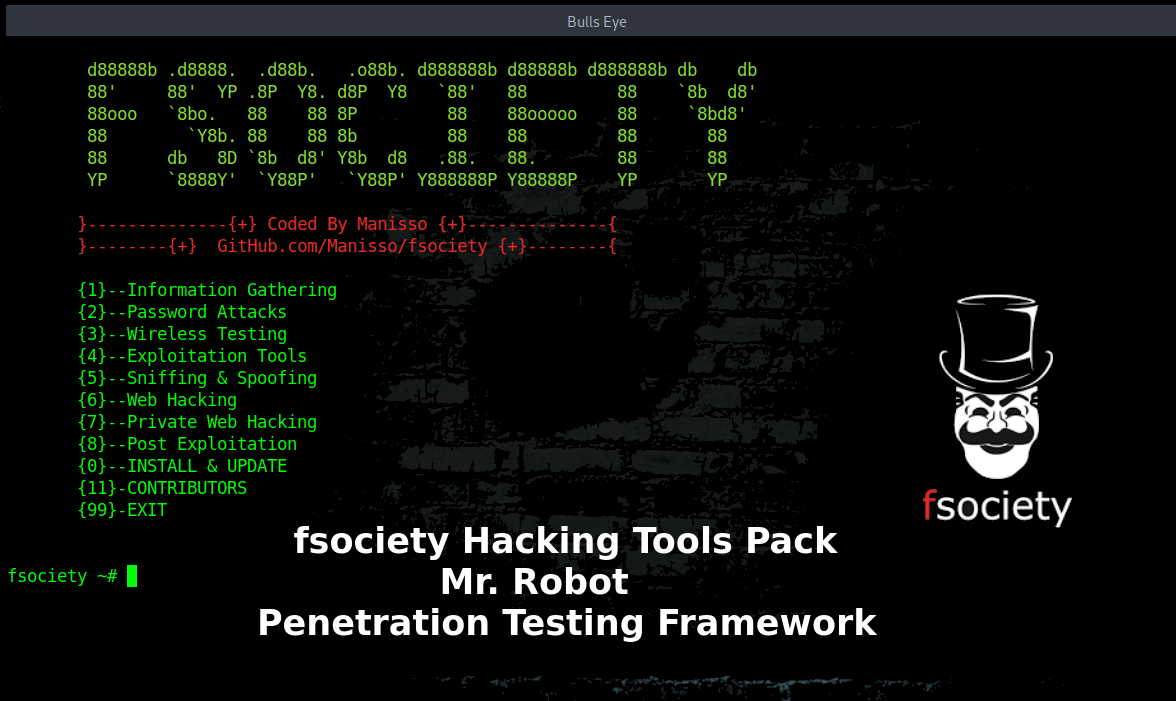
fsociety A Penetration Testing Framework, you will have every script that a hacker needs.
fsociety is a penetration testing framework consists of all penetration testing tools that a hacker needs. It includes all the tools involved in the Mr. Robot Series.
fsociety is the name of a hacker group based in Coney Island, New York, led by the mysterious Mr. Robot. Its name is a play on both the derelict amusement park building in which it has its headquarters and their message: “f**k society.
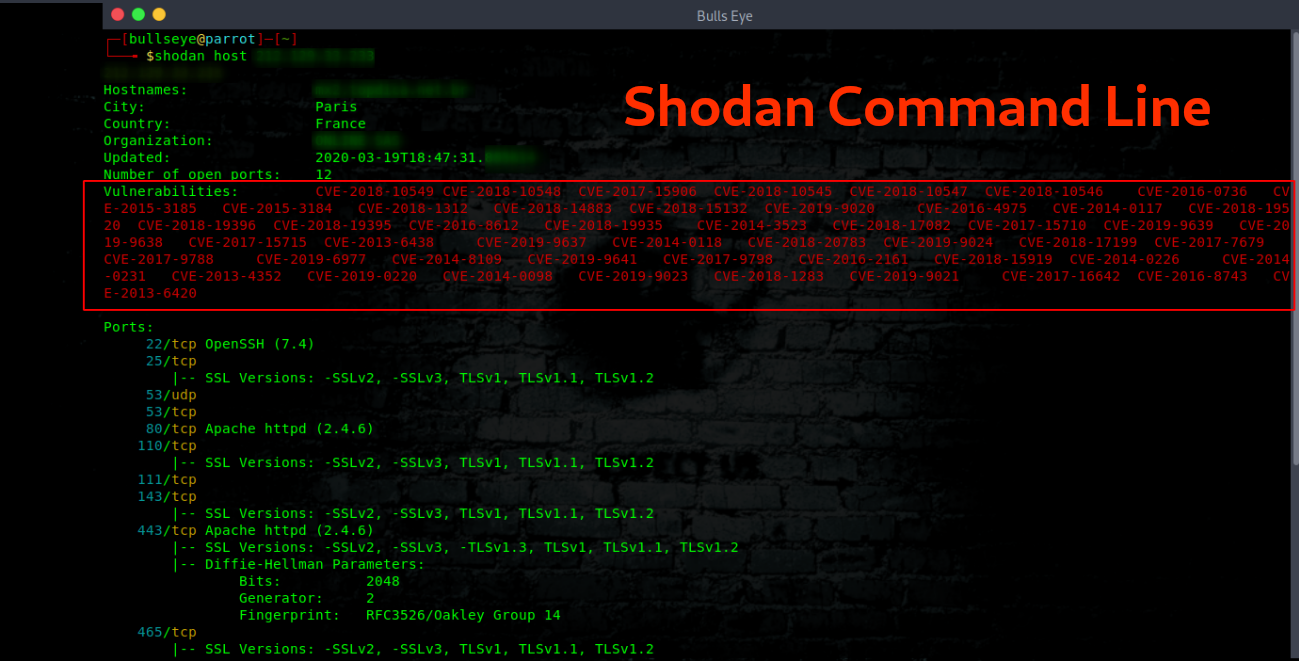
Shodan Command line in this article and video, I show you what you can do, and the benefit of using the Shodan command line in your terminal. Searching for Vulnerabilities to port scanning, there is an incredible amount possible with Shodan.
What is Shodan Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc …) currently connected to the internet using a variety of filters.
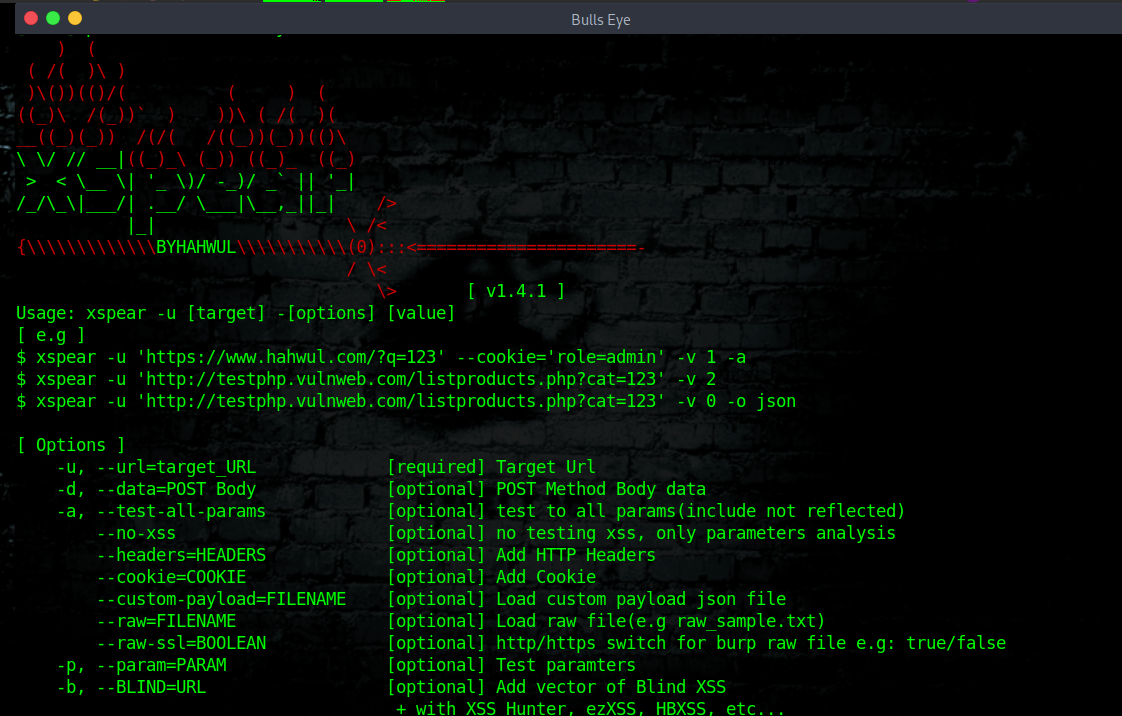
Xspear is a very powerful XSS scanning and parameter analysis tool on ruby gems, capable of both static and dynamic XSS vulnerability analysis.
In this article and video, I will show you how to install and use Xspear. This awesome tool has the ability to scan, detect and analyze potential XSS vulnerabilities on web applications.
What is (XSS) Cross-site Scripting XSS is one of the most common hacking technique when it comes to web application vulnerabilities, and occurs when a web app generates an output based on user input.
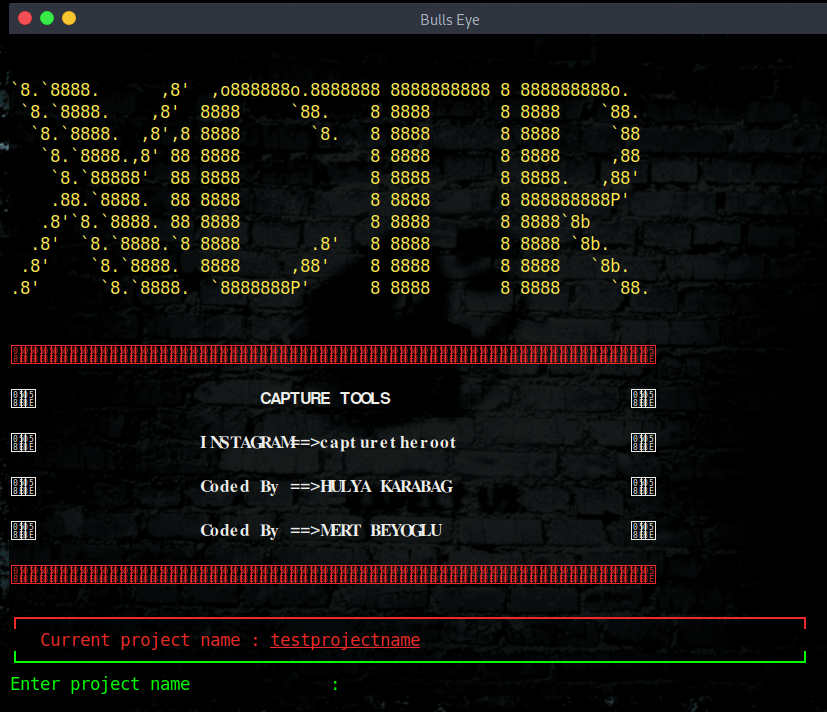
XCTR Hacking Tools is a collection of great Tools: Dork Finder, Admin Panel Finder, Cms Finder, Reverse Ip, Page Viewer, and a Proxy Finder A Step-by-Step walkthrough..!
Sometimes you come across a tool that is worth mentioning. XCTR Hacking Tools is one of them. In this article and video, I show you the options and how to install this tool.
This tool is written by Hulya Karabag | Mert Beyoglu
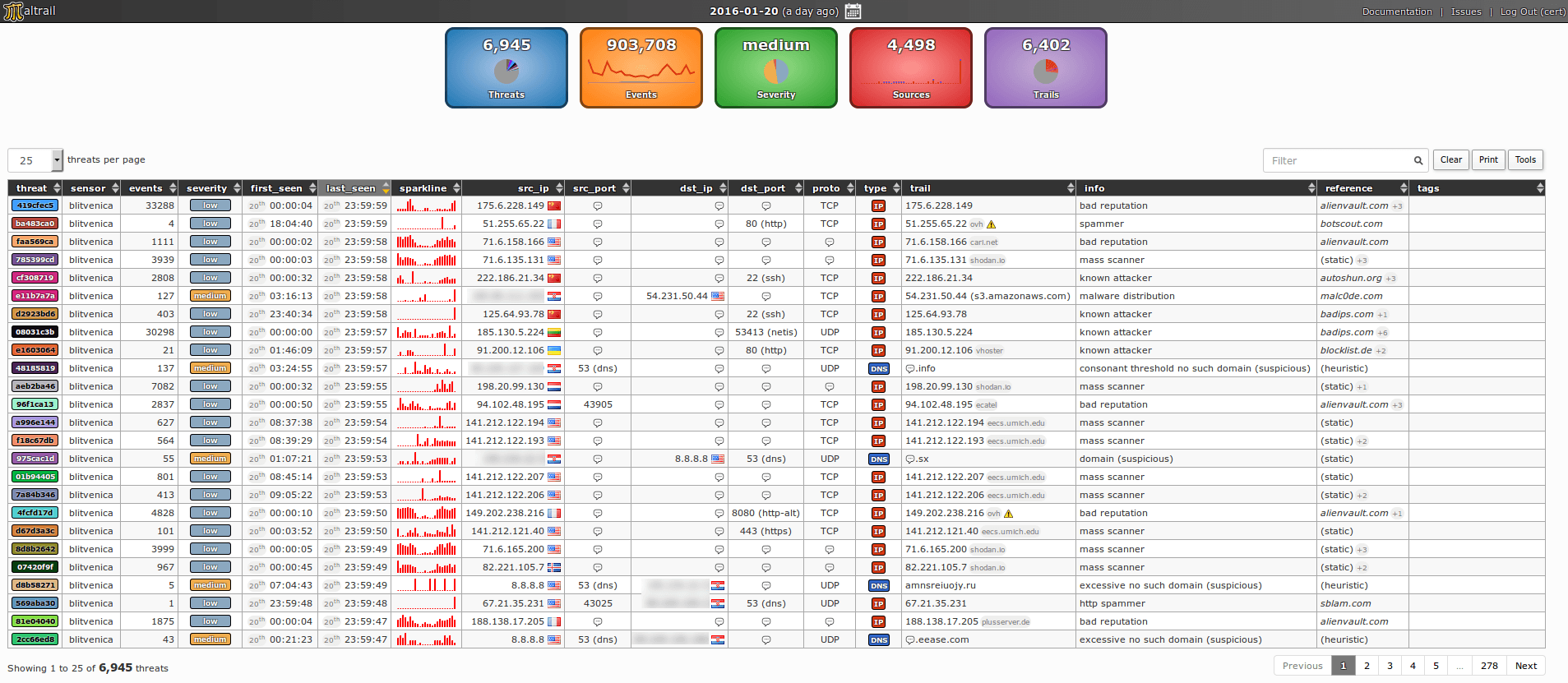
Maltrail is a Malicious Traffic Detection System that utilizes publicly available blacklists (and other trails from various AV reports and user-defined lists) to help discover unknown threats by monitoring traffic against those lists. Maltrail is run from the command line but does include a handy (and optional) web interface.
If you take the security of your servers and computers really seriously, then you know how important it is to be constantly alert to malicious behavior.
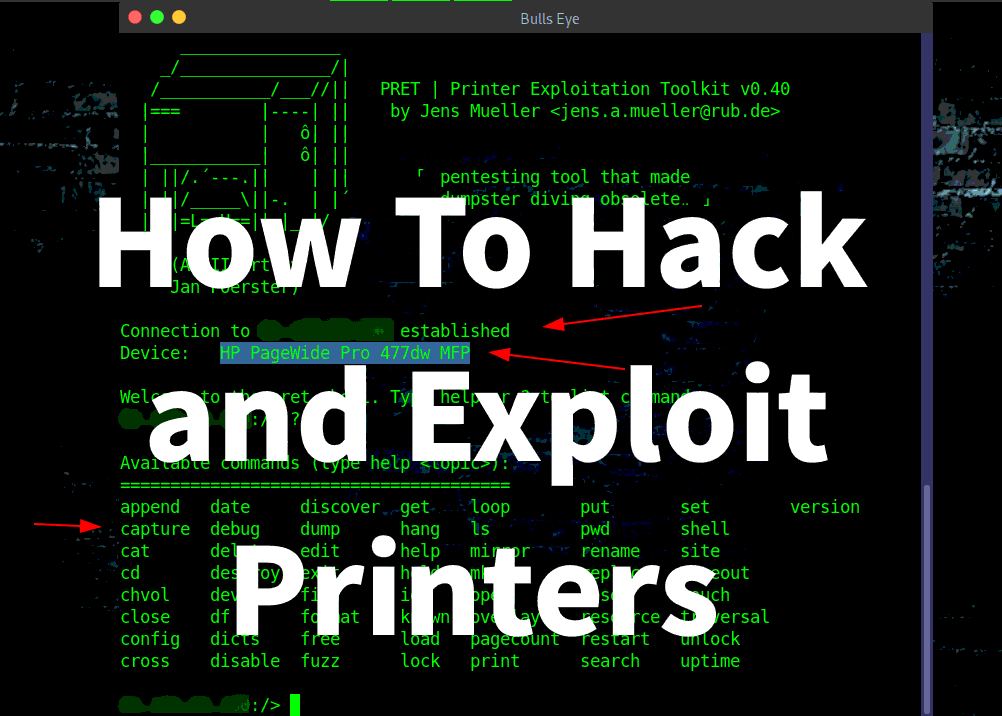
A Step-by-Step walkthrough..! In this article and video, I will show you how to hack and exploit printers. How easy it is to hack, how to get full control, capture, and start sending documents our way. So all future print jobs that are going to come across the printer we’ve connected to which are going to start spooling over.
Why I chose to show you this Again… I chose to show you this, because it is so incredibly easy to hack printers, and through this hack to get further in systems and can cause incredible damage.
Windows is a common operating system used by billions of people. And because of that, there are always many vulnerabilities on Windows.
Because in the future I will use, show and exploit a lot of those vulnerabilities, Therefore I think it is necessary to show the setup of Windows in VirtualBox.
For beginners, but also for advanced people who like to watch and discover maybe something new.
“Difference between a virus and windows?